Description
Challenge #T0048
Digital Duplicates
Author: Jeff Echlin
Framework Category: Investigate
Specialty Area: Digital Forensics
Work Role: Law Enforcement/Counter Intelligence Forensics
Task Description: Create a forensically sound duplicate of the evidence (i.e., forensic image) that ensures the original evidence is not unintentionally modified, to use for data recovery and analysis processes. This includes, but is not limited to, hard drives, floppy diskettes, CDs, PDAs, mobile phones, GPS, and all tape formats.
Scenario
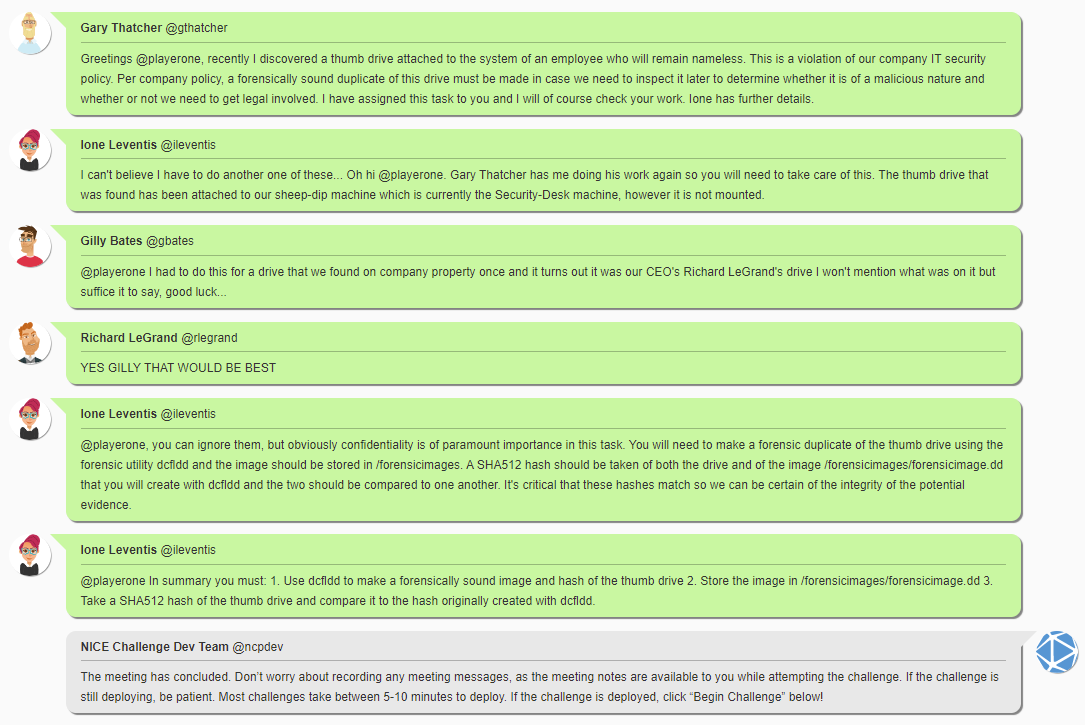
Recently Gary Thatcher our senior system administrator, came across a thumb drive attached to an employee’s system. According to the employee, the thumb drive was attached without their consent and they are unsure of the origin of said drive. The drive was passed to Ione Leventis one of our security analysts. Ione has attached the drive to our sheep-dip system which in our case is the Security-Desk machine. However, Ione was called away on other matters and you are now entrusted with the task. According to current company policy the thumb drive must be inspected for any malicious agents that could threaten DAS Web’s overall security. Your job is to create a forensically sound duplicate image of the thumb drive using dcfldd so it can be examined without the risk of inadvertently modifying potential evidence. SHA512 hashes should also be taken and compared between the original thumb drive which is already attached, but not mounted, to the system and the forensic image.
Additional Information
More details and objectives about this challenge will be introduced during the challenge meeting, which will start once you begin deploying the challenge.
You will be able to check your progress during this challenge using the check panel within the workspace once the challenge is deployed. The checks within the check panel report on the state of some or all of the required tasks within the challenge.
Once you have completed the requested tasks, you will need to document the methodology you used with as much detail and professionalism as necessary. This should be done on the documentation tab within the workspace once the challenge is deployed. Below the main documentation section be sure to include a tagged list of applications you used to complete the challenge.
Your username/password to access all virtual machines and services within the workspace will be the following…
Username: playerone
Password: password123
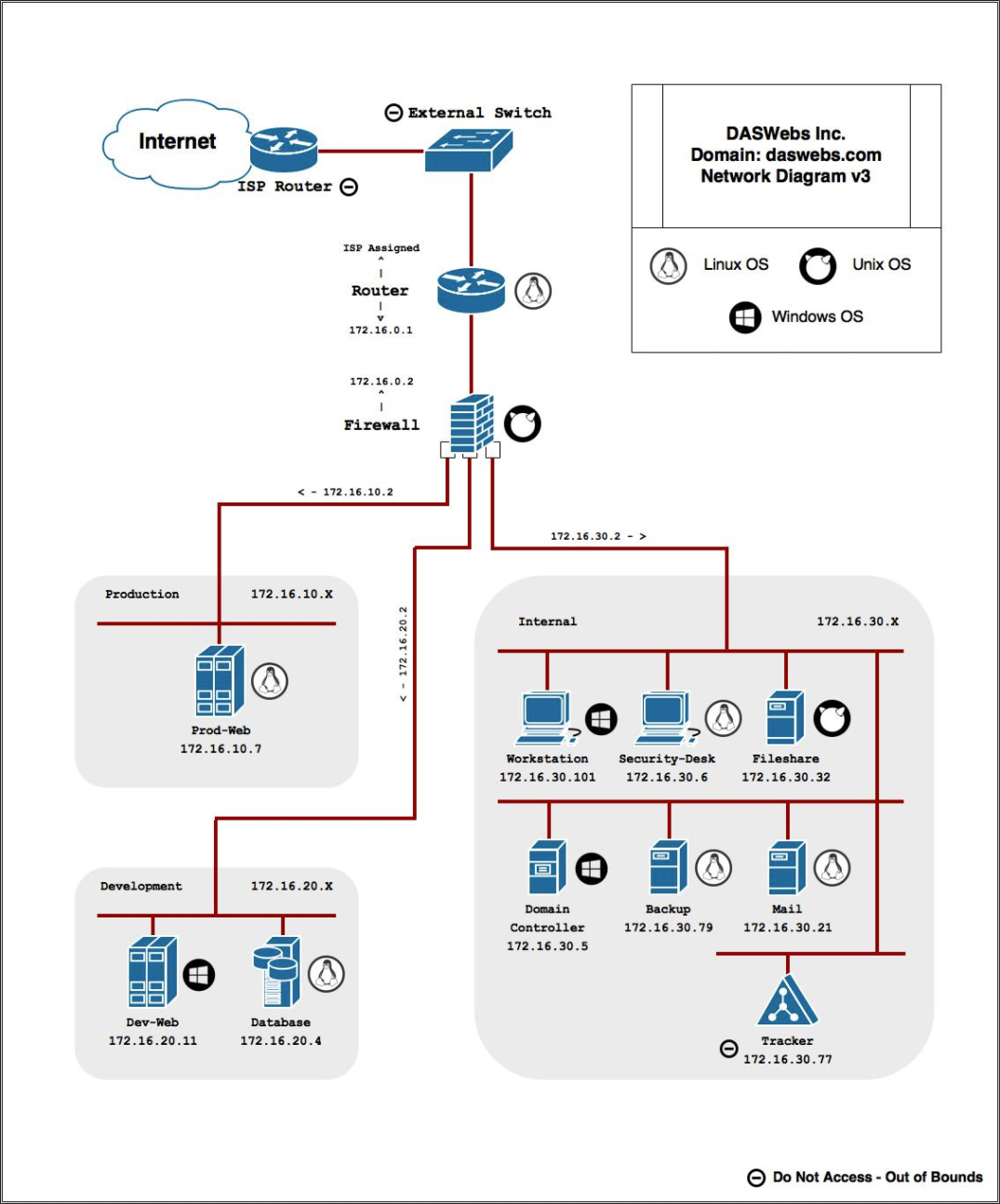
Network Map
Meeting
NICE Framework & CAE KU Mapping
NICE Framework KSA
K0017. Knowledge of Concepts and Practices of processing digital forensic data.
K0021. Knowledge of data backup and recovery.
K0042. Knowledge of incident response and handling methodologies.
K0060. Knowledge of operating systems.
K0117. Knowledge of file system implementations (e.g., New Technology File Systems [NTFS], File Allocation Table [FAT], File Exention [EXT]).
K0118. Knowledge of processes for seizing and preserving digital evidence.
K0122. Knowledge of investigative implications of hardware, Operating Systems, and nework technologies.
K0132. Knowledge of which system files (e.g., log files, registry files, configuration files) contain relevant informaiton and where to find those system files.
K0133. Knowledge of types of digital forensics data and how to recognize them.
K0304. Knowledge of concepts and practices of processing digital forensic data.
S0047. Skill in preserving evidence integrity according to standard operating proccedures or national standards.
S0065. Skill in identifying and extracting data of forensic interest in diverse media (i.e., media forensics).
S0067. Skill in identifying, modifying, and manipulating applicable system components within Windows, Unix, or Linux (e.g., passwords, user accounts, files).
S0073. Skill in using virtual machines. (e.g., Microsoft Hyper-V, VMWare vSphere, Citrix XenDesktop/Server, Amazon Elastic Compute Cloud, etc.).
S0089. Skill in one-way hash functions (e.g., Secure Hash Algorithm [SHA], Message Digest Algorithm [MD5]).
CAE Knowledge Units
Cybersecurity Principles
Digital Forensics
IT Systems Components
Operating Systems Concepts
NICE Framework 1.0 Mapping (August 2012 - August 2017)
NICE Framework 1.0 KSA
Skill in preserving evidence integrity according to standard operating procedures or national standards.
Knowledge of basic concepts and practices of processing digital forensic data.
Knowledge of file system implementations (e.g., New Technology File System [NTFS], File Allocation Table [FAT], File Exention [EXT]).
Knowledge of data backup, types of backups (e.g., full, incremental), and recovery concepts and tools.
Knowledge of processes for seizing and preserving digital evidence (e.g., chain of custody).
Knowledge of which systems files (e.g., log files, registry files, configuration files) contain relevant information and where to find those system files.
Skill in using virtual machines.
Knowledge of incident response and handling methodologies.
Knowledge of operating systems.
NICE Framework 1.0 Compentencies
Computer Forensics
Cryptography
Data Management
dcfldd
Example
1
2
3
4
dcfldd if=/dev/sdb1 of=/media/disk/test_image.dd hash=md5,sha1 hashlog=/media/disk/hashlog.txt
# Hash verification
dcfldd if=/dev/sdb1 vf=/media/disk/test_image.dd verifylog=/media/disk/verifylog.txt
Challenge - Image /dev/sdb1
1
dcfldd if=/dev/sdb1 of=/forensicimages/forensicimage.dd hash=sha512 hashlog=/forensicimages/forensicimage.txt
- Use dcfldd to make a forensically sound image and hash of the thumb drive 2. Store the image in /forensicimages/forensicimage.dd 3. Take a SHA512 hash of the thumb drive and compare it to the hash originally created with dcfldd.
1
dcfldd if=/dev/sdb1 vf=/forensicimages/forensicimage.dd verifylog=/forensicimages/forensicimage.txt
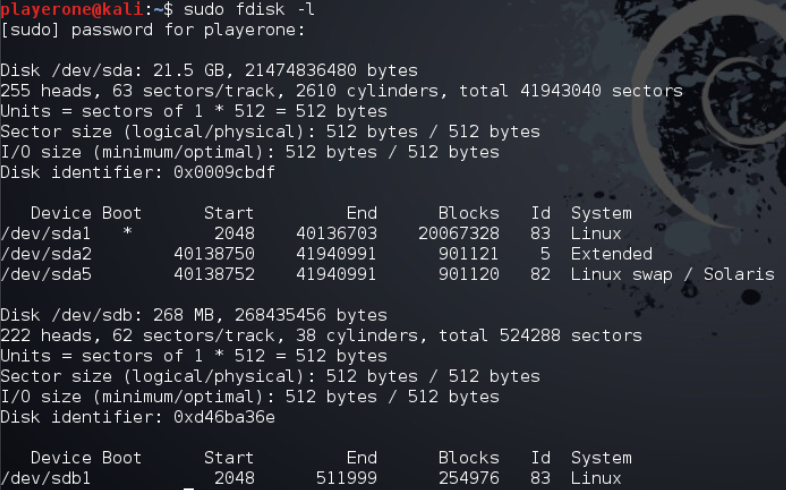
Find the disk and change permissions to read only
Disk drives attached to machine
1
sudo fdisk -l
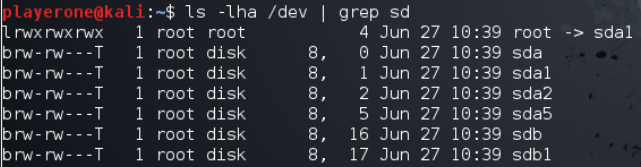
List permissions on /dev/sd*
1
ls -lha /dev | grep sd
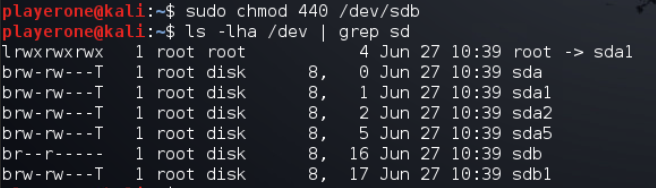
Change permissions on /dev/sdb to read only
1
2
sudo chomd 440 /dev/sdb
ls -lha /dev | grep sd
Create /forensicimages folder
1
sudo mkdir /forensicimgages
/forensicimages/forensicimage
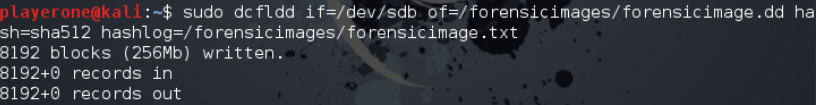
Image USB drive
1
sudo dcfldd if=/dev/sdb of=/forensicimages/forensicimage.dd hash=sha512 hashlog=/forensicimages/forensicimage.txt
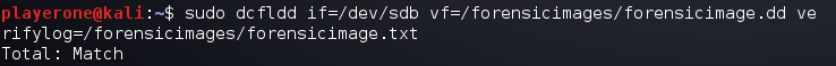
Verify hash
1
sudo dcfldd if=/dev/sdb vf=/forensicimages/forensicimage.dd verifylog=/forensicimages/forensicimage.txt
Summary
Tools:
1
2
3
4
5
6
fdisk
ls
grep
chmod
mkdir
dcfldd
Machines used:
1
Security-Desk
I began the challenge and found the drive attached to the machine using “sudo fdisk -l”. This command listed the drives the system sees and the partitions.
Next I checked the permissions on /dev/sdb, currently set to read/write, with the command ls -lha /dev | grep sd.
Then I change the permission to read-only on the disk using the command sudo chmod 440 /dev/sdb.
I checked for the existence of the forensicimages folder off root and was not found ls /, issued the command sudo mkdir /forensicimages to create the folder.
I then imaged the drive using the following command: sudo dcfldd if=/dev/sdb of=/forensicimages/forensicimage.dd hash=sha512 hashlog=/forensicimages/forenicimage.txt
Verified the image with the following command: sudo dcfldd if=/dev/sdb vf=/forensicimages/forensicimage.dd verifylog=/forensicimages/forensicimage.txt
I confirmed the match of the sha512 signature of the drive and image.