Description
Challenge #T0297
Properly Prioritized Web Watching
Author: Bailey Kasin
Framework Category: Protect and Defend
Specialty Area: Cybersecurity Defense Analysis
Work Role: Cyber Defense Analyst
Task Description: Identify applications and operating systems of a network device based on network traffic.
Scenario
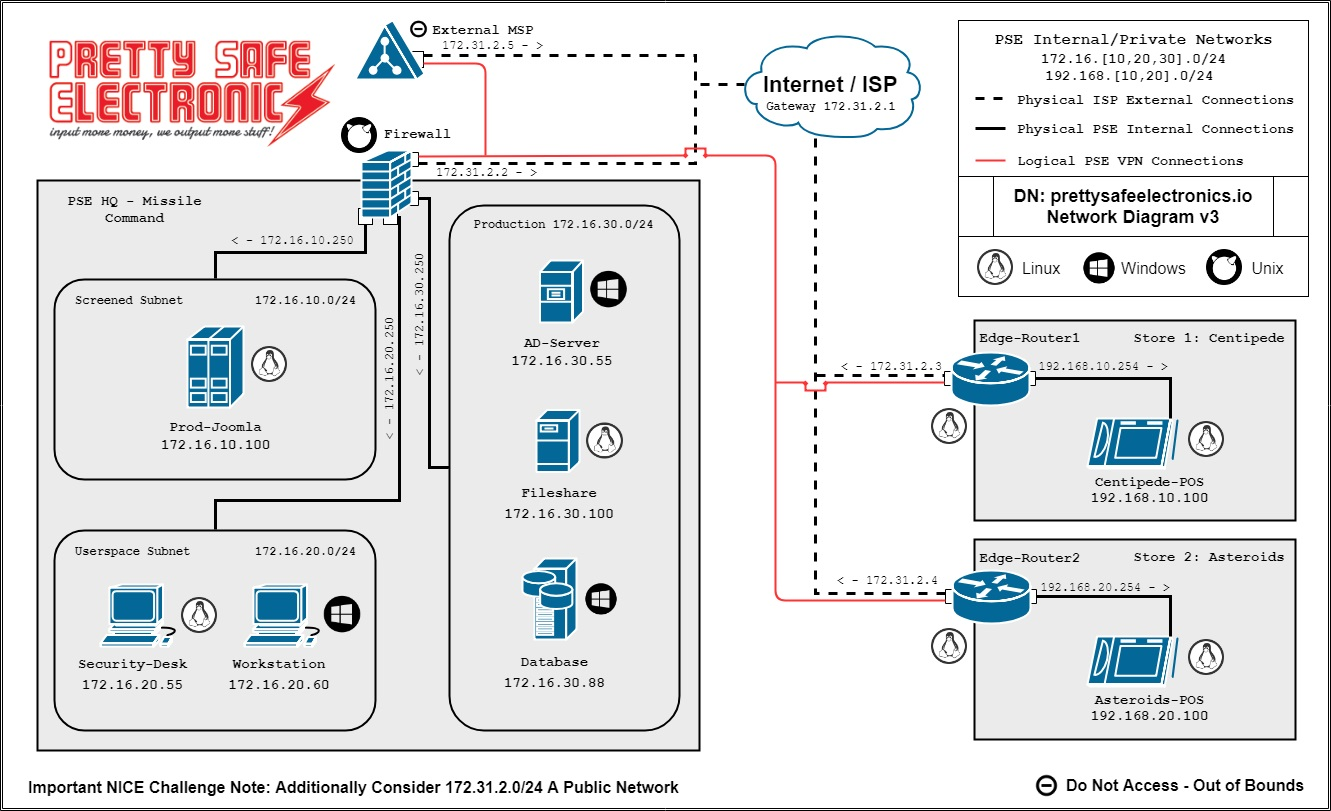
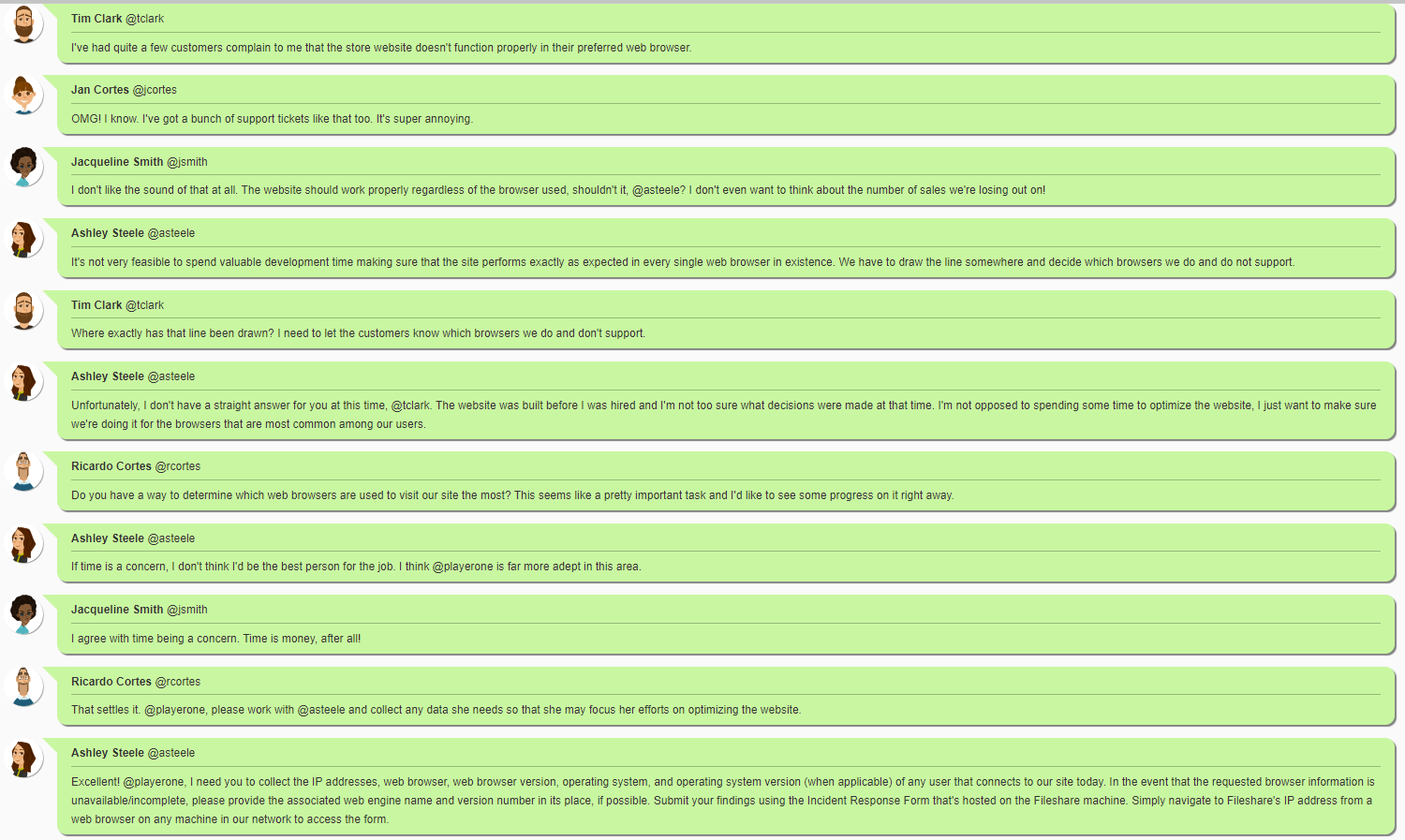
Jan Cortes and Tim Clark have been dedicating too much time to support tickets for the website being broken. We can’t make it work on every browser, so we need you to watch the traffic to our website so we know which web browsers to dedicate time to supporting.
Additional Information
More details and objectives about this challenge will be introduced during the challenge meeting, which will start once you begin deploying the challenge.
You will be able to check your progress during this challenge using the check panel within the workspace once the challenge is deployed. The checks within the check panel report on the state of some or all of the required tasks within the challenge.
Once you have completed the requested tasks, you will need to document the methodology you used with as much detail and professionalism as necessary. This should be done on the documentation tab within the workspace once the challenge is deployed. Below the main documentation section be sure to include a tagged list of applications you used to complete the challenge.
Your username/password to access all virtual machines and services within the workspace will be the following… Username: playerone Password: password123
The username/password used to access the Firewall’s web interface within the workspace will be the following… Username: admin Password: password123
The web form used for this challenge accepts a limited number of entries.
Network Map
Meeting
NICE Framework & CAE KU Mapping
NICE Framework KSA
A0159. Ability to interpret the information collected by network tools (e.g. Nslookup, Ping, and Traceroute).
K0001. Knowledge of computer networking concepts and protocols, and network security methodologies.
K0058. Knowledge of network traffic analysis methods.
K0060. Knowledge of operating systems.
K0061. Knowledge of how traffic flows across the network (e.g., Transmission Control Protocol [TCP] and Internet Protocol [IP], Open System Interconnection Model [OSI], Information Technology Infrastructure Library, current version [ITIL]).
K0111. Knowledge of network tools (e.g., ping, traceroute, nslookup)
K0221. Knowledge of OSI model and underlying network protocols (e.g., TCP/IP).
K0301. Knowledge of packet-level analysis using appropriate tools (e.g., Wireshark, tcpdump).
S0156. Skill in performing packet-level analysis.
CAE Knowledge Units
Basic Cyber Operations
Basic Networking
Network Forensics
Operating Systems Concepts
Summary
Applications used:
1
2
Linux: su, nano, tail
Windows: putty, notepad, FireFox
Installed putty on Workstation-Desk. Launched a SSH session to 172.16.10.100. Logged in with “playerone password123” and switch user to root “su”. Edited the configuration file for the Joomla site, nano /etc/apache2/sites-enabled/joomla.conf. Added LogFormat "%h %l %u %t \"%r\" %>s %O \"%{Referer}i\" \"%{User-Agent}i\"" combined and changed CustomLog to remove “common” and changed it to “combined”. Saved and exited nano. Restarted apache service by apachectl restart. 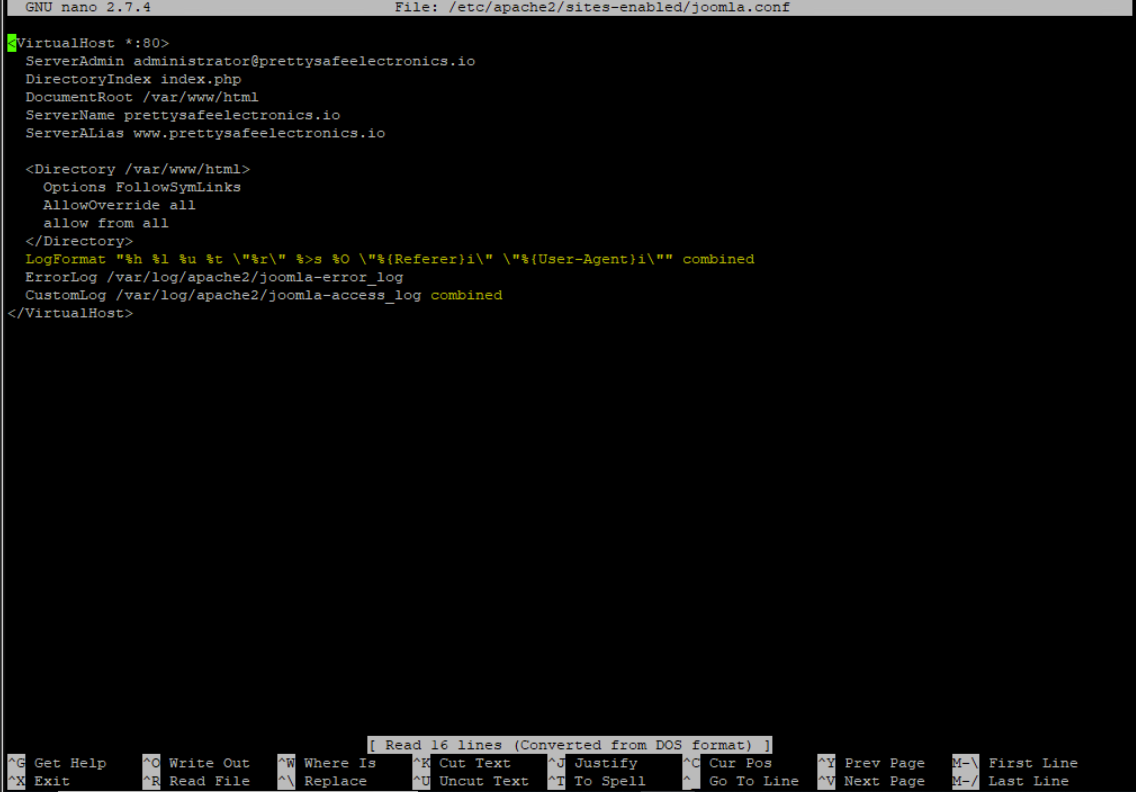
Checked log tail -f /var/log/apache2/joomla-access_log, the tail -f will continully monitor the file for changes. Saw the updates of the 4 IP’s and their connections strings. Copied this from the terminal to notepad. 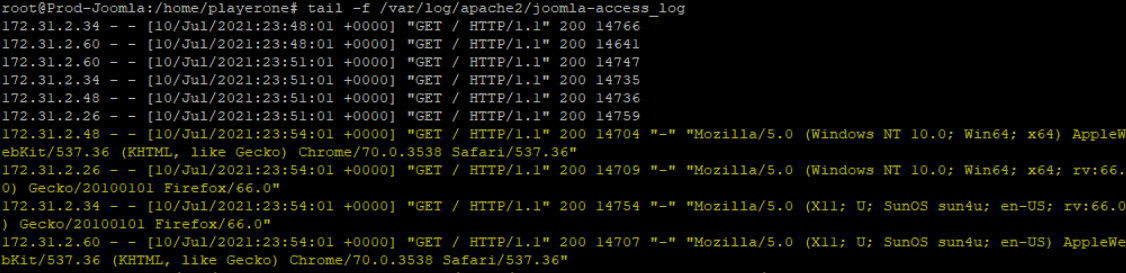
Navagated in FireFox to the fileserver IP 172.16.30.100. Entered in the submissions for the requested information (IP Address, Browers, Browser Version, Operating system name, Operating system version).
Submission 1: 172.31.2.48, Chrome, 70.0.3538, Windows, 10 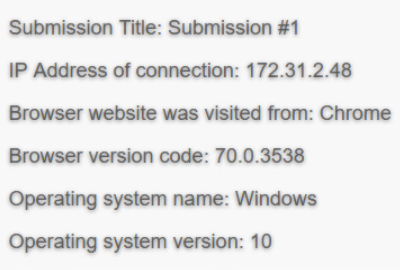
Submission 2: 172.31.2.26, Firefox, 66.0, Windows, 10 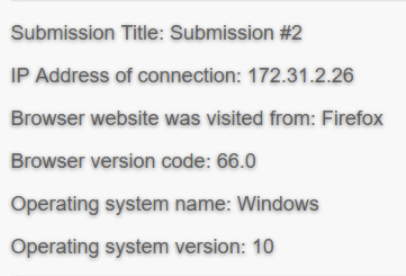
Submission 3: 172.31.2.34, Firefox, 66.0, SunOS, NA 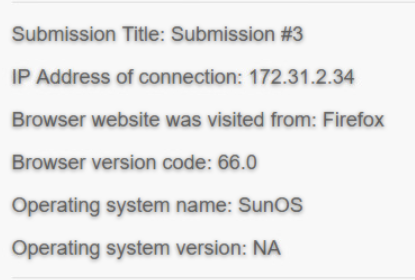
Submission 4: 172.31.2.60, Chrome, 70.0.3538, SunOS, NA 
All checkpoints turned green marking the desiered state is good.
1
2
LogFormat "%h %l %u %t \"%r\" %>s %O \"%{Referer}i\" \"%{User-Agent}i\"" combined
CustomLog logs/access.log combined